
10 Hours of Expert Video Instruction Overview This course is a complete guide to help you get up and running with your cybersecurity career. You will learn the key tenets and fundamentals of ethical hacking and security penetration testing techniques.
External Penetration Test . An External Penetration Test differs from a vulnerability assessment in that it actually exploits the vulnerabilities to determine what information is actually exposed to the outside world. An External Penetration Test mimics the actions of an actual attacker exploiting weakne
Manage your application security with Security Compass’ software security requirements management platform. We offer OWASP top 10 & cyber security training.
CyberTest is independent cyber security testing, research and development firm that offers security consulting and penetration testing services that helps organizations and businesses securing their assets
Understand what is penetration testing and why it is important to spend money to identify security vulnerabilities in your applications.

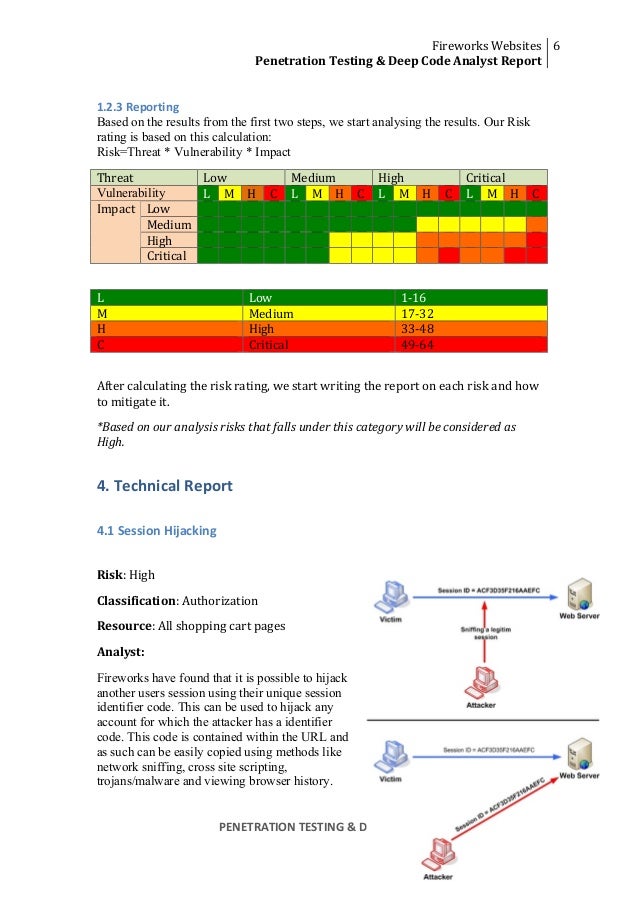
The overall methodology for penetration testing can be broken into a three-step process: network enumeration, vulnerability analysis, and exploitation.
SecurityFocus is designed to facilitate discussion on computer security related topics, create computer security awareness, and to provide the Internet’s largest and most comprehensive database of computer security knowledge and resources to the public.
Dec 01, 2015 · The U.S. Department of Homeland Security (DHS) has been quietly launching stealthy cyber attacks against a range of private U.S. companies — mostly banks and energy firms. These digital intrusion attempts, commissioned in advance by the private sector targets themselves, are part of a little
Advanced penetration testing services for companies with hardened networks. Need professional security assessment services? Call our pen test team today!
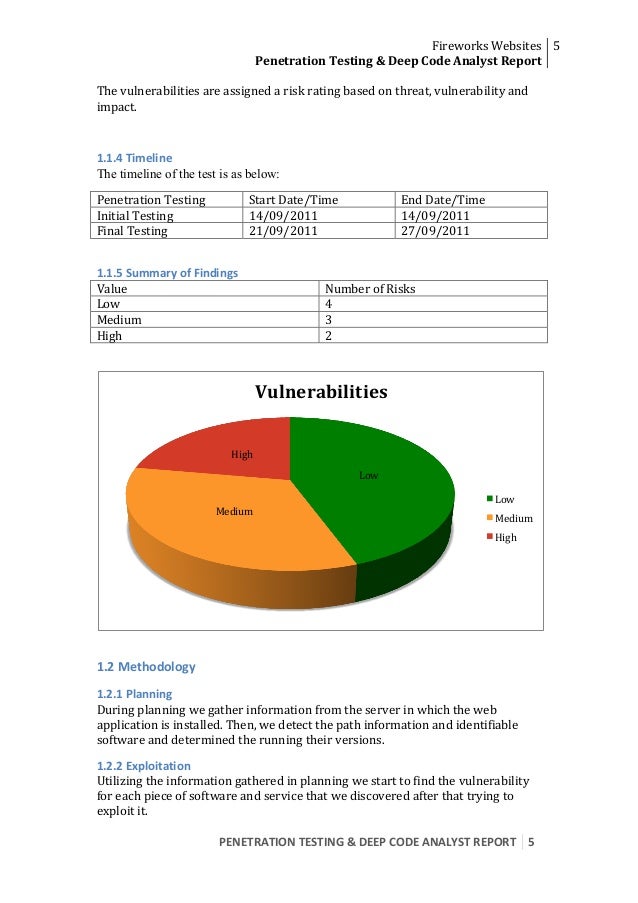
It’s important for all organizations to periodically assess and test security vulnerabilities, to better evaluate risk and be ready to detect, prevent and respond to …